
Photo by Glenn Carstens-Peters on Unsplash
Connecting GitHub Container Registry with Azure Red Hat OpenShift
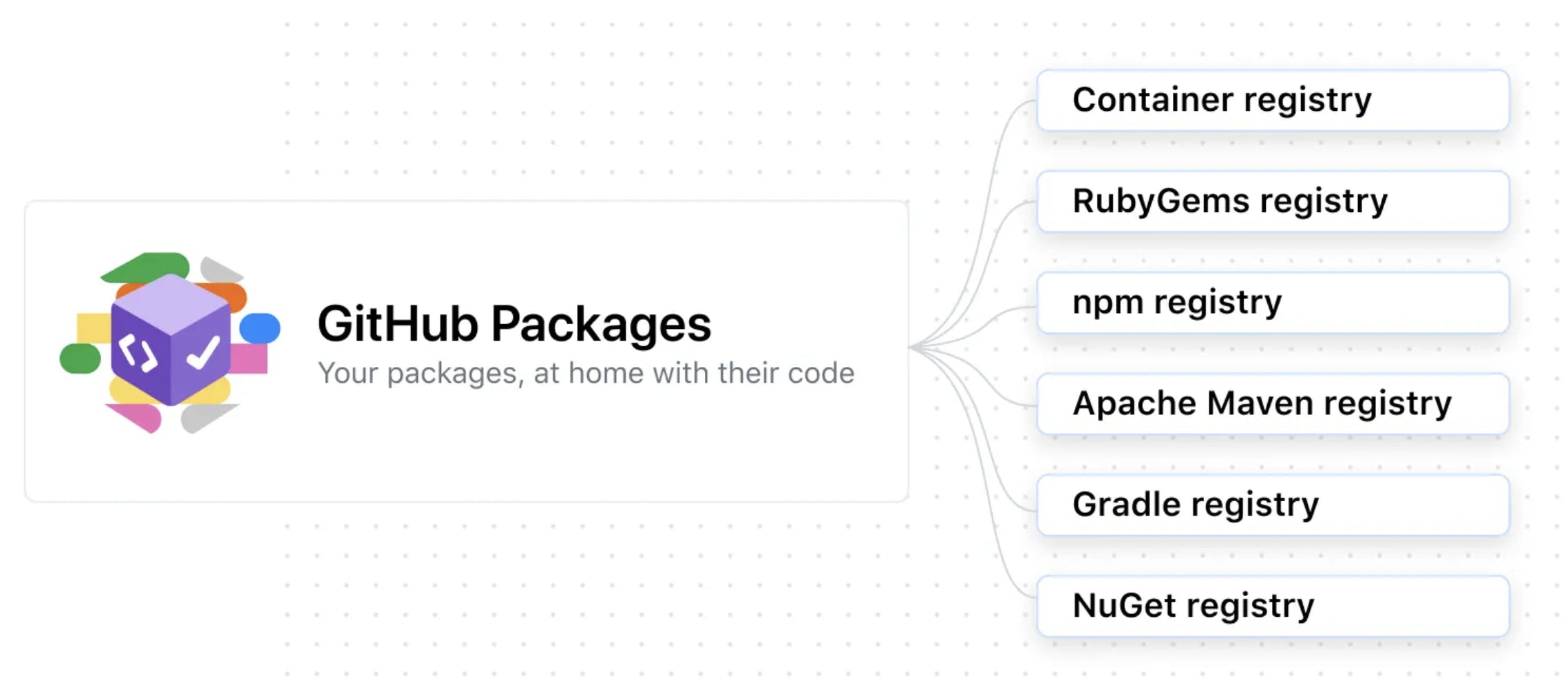
GitHub packages let you host your packages — be it container images, npm packages or NuGet packages. It is free for public repositories and has 500MB of free storage for private repositories.
In this quick post, we will see how to connect to GitHub packages to pull our container images and deploy the application in Azure Red Hat OpenShift.
Publishing image
I will skip this step for this post, but the documentation is clear and I followed the exact steps to publish a sample NodeJS application to the container registry.
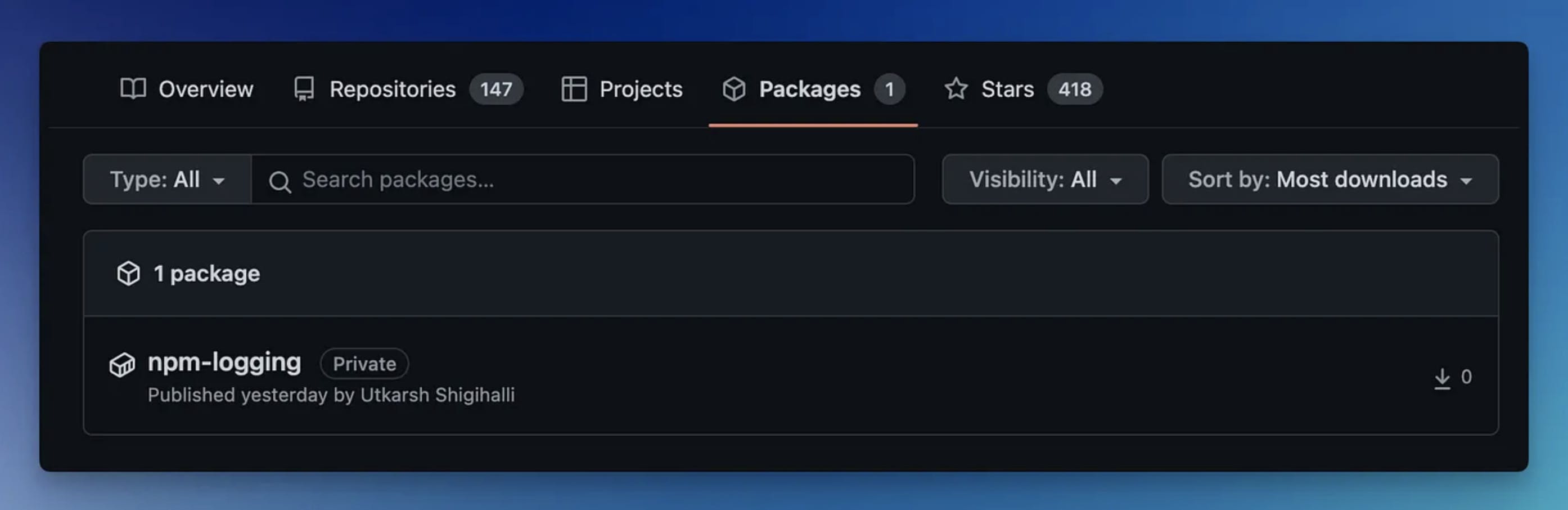
Connecting GitHub container registry with ARO (Azure Red Hat OpenShift)
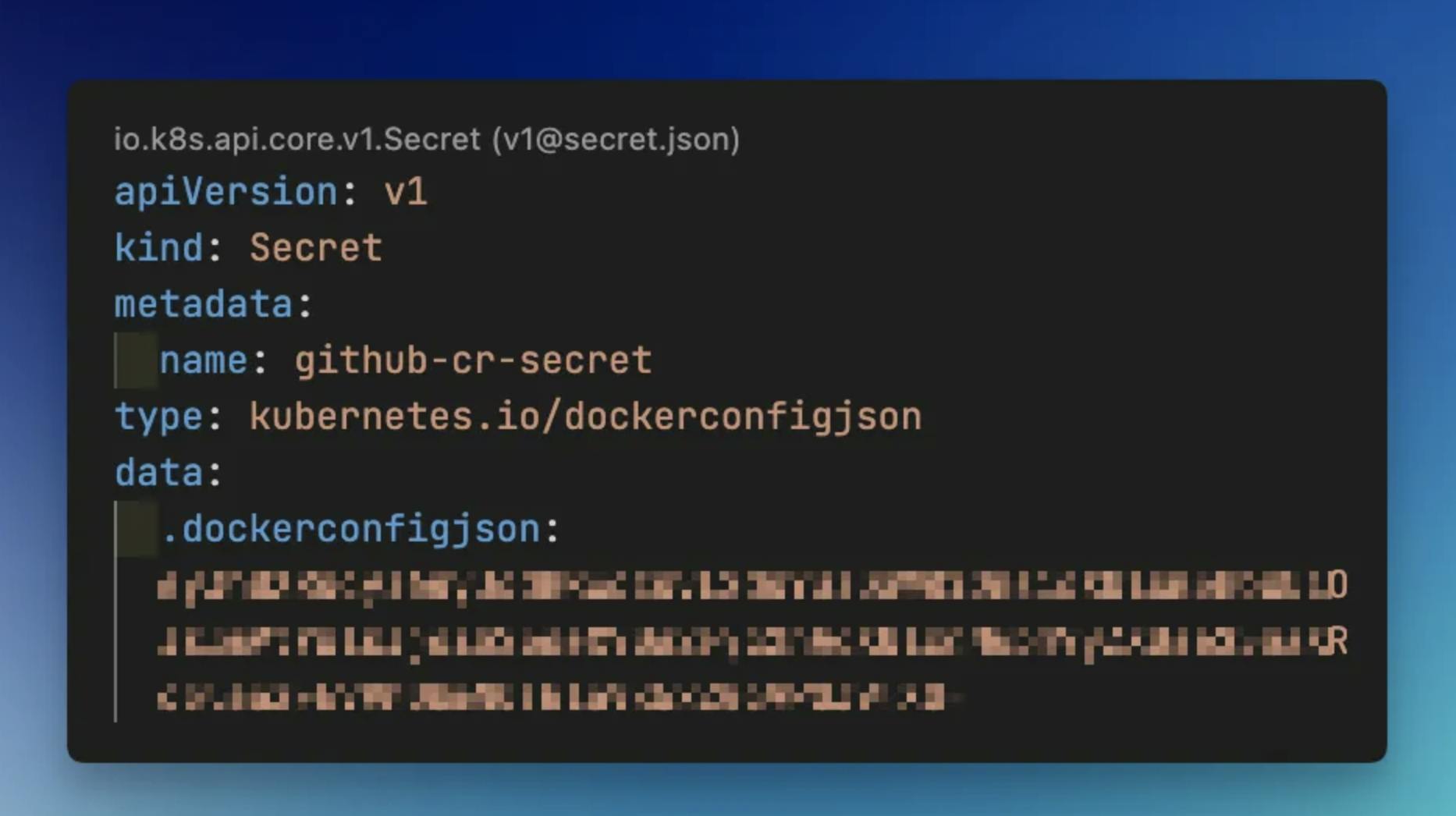
Kubernetes service connects to container registries using image pull secrets. ARO is no different, be it Azure Container Registry (ACR) or GitHub Container Registry, we will need to create a Kubernetes secret which has auth information for the Kubernetes to pull images.
We start by creating a manifest imperatively using CLI and get a YAML so that we can apply it.
kubectl create secret docker-registry github-cr-secret --docker-server=https://ghcr.io --docker-username=<username> --docker-password=$GH_PAT --docker-email=<email-address> --dry-run=client -o yaml > ./k8s/pullsecret.yml
GH_PAT is the environment variable which holds the classic GitHub PAT token with read/write and delete packages permission. You can follow this documentation if you need instructions on how to do it.
You will have a new manifest file named pullsecret.yml created.
The next step involves connecting to ARO and applying the manifest so that a secret is created in ARO.
Connect to your ARO console and copy the login command and log in using the terminal.
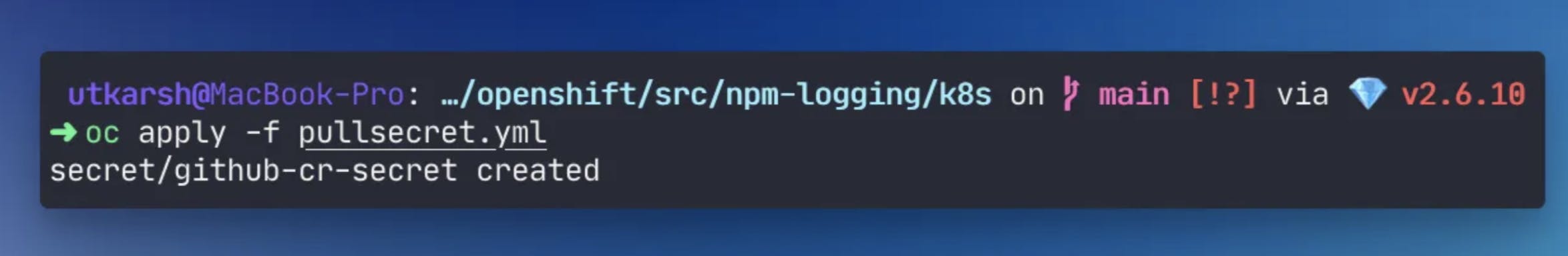
We can then apply the image pull secret to our cluster using the oc command line oc apply -f <file.yml>
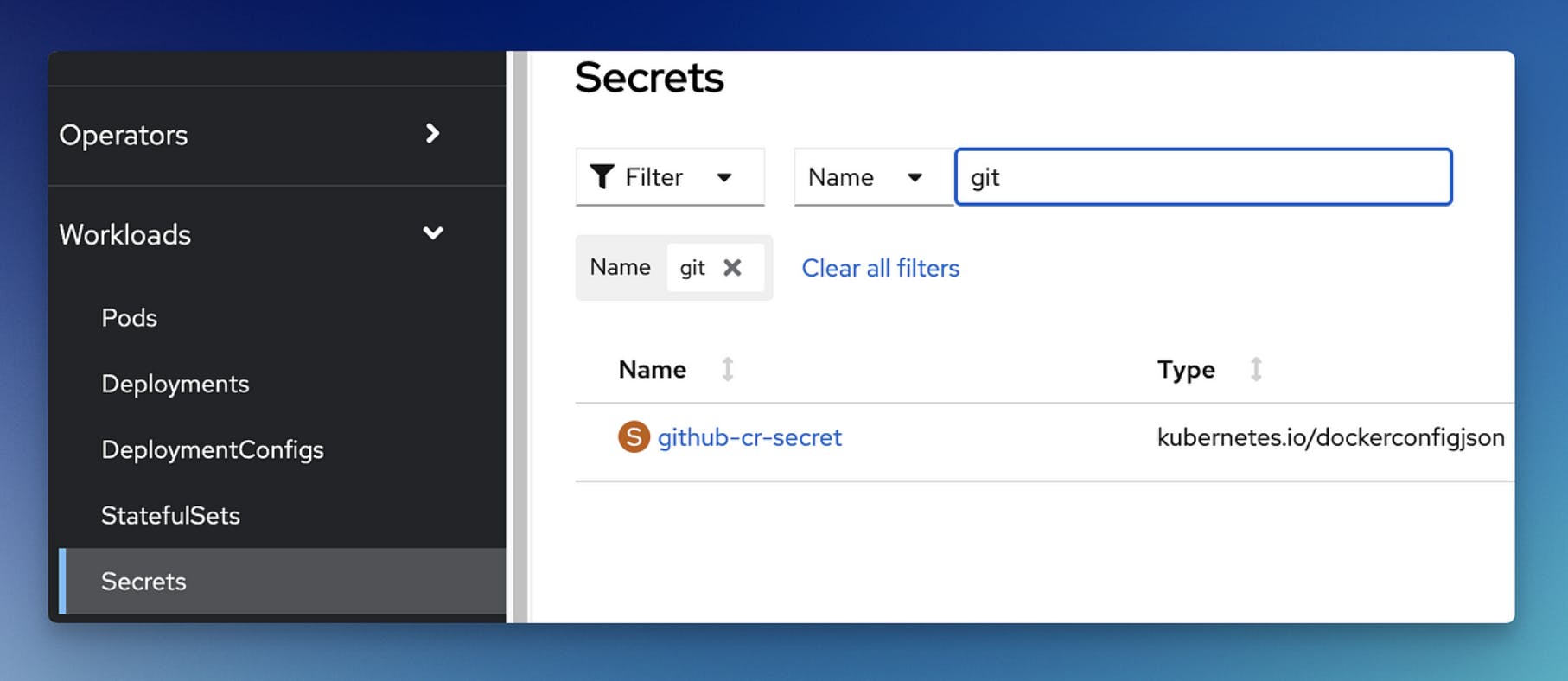
If you head over to the web console, you will see the secret created.
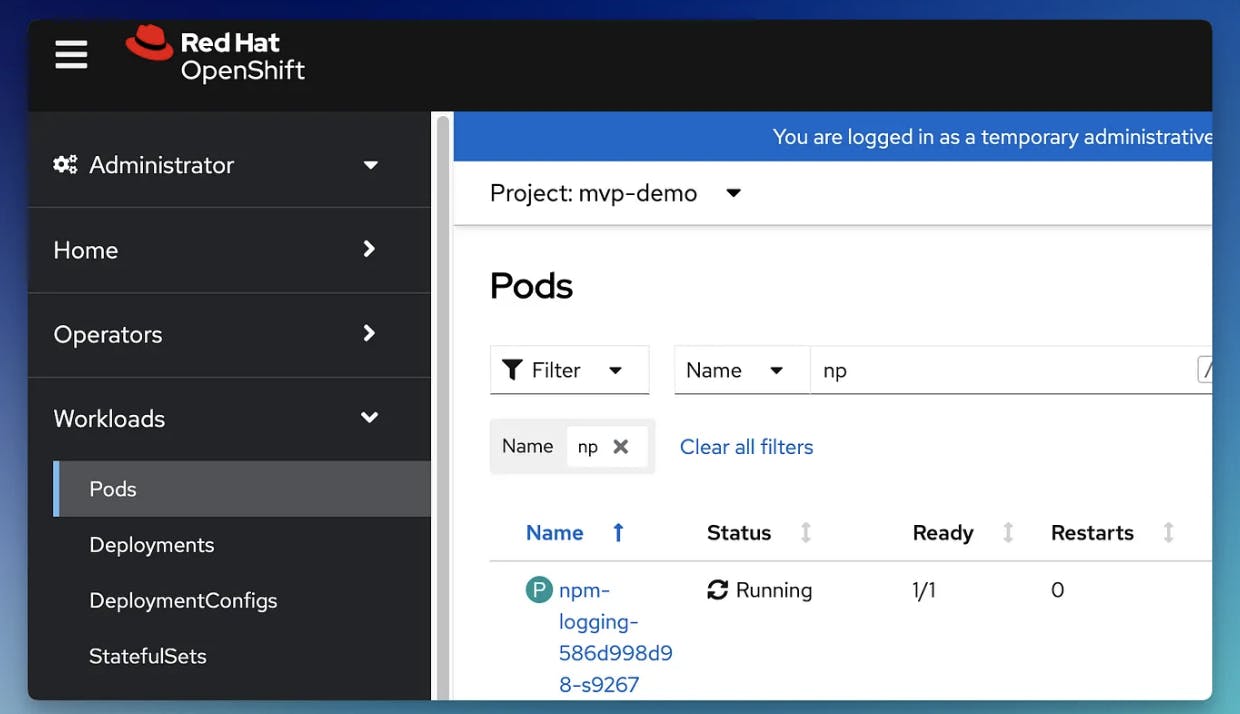
Deploying sample app and testing pull secret
Let us now create a Kubernetes deployment for our app and point to the image published in the GitHub container registry.
# deploy.yml
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app: npm-logging
name: npm-logging
spec:
replicas: 1
selector:
matchLabels:
app: npm-logging
template:
metadata:
labels:
app: npm-logging
spec:
containers:
- image: ghcr.io/onlyutkarsh/npm-logging:0.0.1
name: npm-logging
imagePullPolicy: Always
resources:
limits:
cpu: 100m
memory: 128Mi
requests:
cpu: 100m
memory: 128Mi
imagePullSecrets:
- name: github-cr-secret
status: {}
Notice, we are referring to the secret under
imagePullSecretselement andimageproperty refers to our published docker image from GitHub Container Registry
Applying this deployment manifest to our cluster (using oc apply -f deploy.yml command) should pull our image from GitHub Container Registry and get our application running.
Conclusion
That’s it, as you saw, connecting to GitHub packages is simple with classic personal access tokens (PAT). However, PAT’s do expire and when they do, you will need to update the secret in OpenShift.
Hope you enjoyed reading this post.

